Well actually day two for me but day one for the conference proper. The day started with the Keynote speech, by Bob Muglia, Senior Vice President of the Server and Tools Business at Microsoft, which I missed, on purpose. Instead I did some email and wrote the first blog entry and hence missed all of the crowds heading to the Orlando Convention Center. I headed out over there just before 10:00am, for the first breakout session at 10:30am.
I attended four sessions today;
- SEC252: Notes from the Field: Implementing a Military Grade Security Access Solution
- SEC355: Privacy: The Why, What, and How
- IDA351: Active Directory Read Only Domain Controller in your Enterprise
- UNC360: Protect. Preserve. Discover. Compliance and governance in Exchange Server 2007
SEC252: Notes from the Field: Implementing a Military Grade Security Access Solution
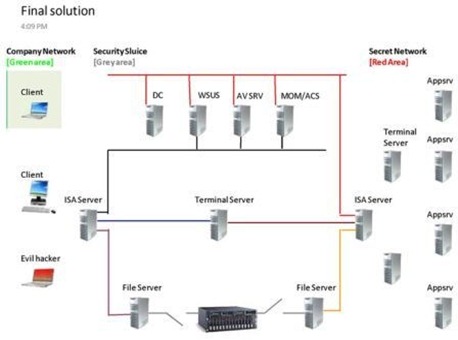
A Swedish company, TrueSec, talked about what they’d done for Volvo and how they’d designed and implemented a capability for Volvo users to be able to connect to a high security (military) network securely. It’s a bit to involved to go in to in this post but in involved an ISA server on the entry point, another ISA server in to the highly secure network. In between the ISA’s is a Terminal Server and inside the secure network was another Terminal Server. Users have certs to gain access through the ISA and use SmartCards to log in to both Terminal Servers, no credential pass though – it wasn’t technically possible. The picture below shows the setup.
SEC355: Privacy: The Why, What, and How
A Steve Riley presentation, always interesting. In this case talking about privacy, what is it, do we have it etc. A couple of things that came out of it that would probably be interesting to look into;
- Block 3rd party cookies, in IE
- use a host file to block Ads etc. Yes I know we have Bluecoat but what about laptop users on travel. (
IDA351: Active Directory Read Only Domain Controller in your Enterprise
I won’t go in to a lot of detail on this one but it does have a lot of potential. Deploying RODC can be done securely without having to have a Domain Admin at the site. It would allow us to reduce the number of Domain Admins we have, deploy RODC in places that we normally wouldn’t think of deploying a DC. It also has potential for intra-company DMZ’s1 and possibly Extranets.
For an intra-company DMZ I’m wondering if it will solve the issue with the SharePoint people picker. Put an RODC in the DMZ to allow it to talk back to a full DC, via IPSec tunnel?, on the internal network. When SharePoint wants to talk to an internal DC it talks to the RODC. I have talked with some Microsoft people here about this. They thought it might work but weren’t sure. I’ll have to go back as they have someone they thought would know more who wasn’t at the desk when I was there. Note! Microsoft Exchange does NOT work with an RODC. It requires write access to a DC. Whilst the RODC can
Some links to RODC resources;
- http://go.microsoft.com/fwlink/?linkid=120840
- http://go.microsoft.com/fwlink/?linkid=120845
- http://blogs.technet.com/natem
1 Intra-company DMZ – This is a DMZ between different parts of a company that are separated by a firewall. This configuration can occur in global company’s, or those that have, for whatever reason, segregated various lines of business using firewalls.
UNC360: Protect. Preserve. Discover. Compliance and governance in Exchange Server 2007
This turned out to be a short session. The presenter went through his material very quickly. Even so there were a number of items that did come out of it;
- All emails go through Transport Hubs, even mailbox to mailbox. This means you can use the Transport hub to apply rules to the message traffic
- You can use rules on the Transport Hub to
- help prevent information leakage (doesn’t inspect attachments though)
- Send NDRs to users saying that their email violated some policy. i.e. put a rule in place to check for SSN and send an NDR. This leads to the question, can you just send a notification to the user but send the email anyway – based on sending an email to the UK?
- Internal email transport is ALL encrypted. As Exchange 2007 supports Mutual TLS it leads to the question, why not use MTLS between the Exchange 2007 server and the perimeter email system. Therefore all email transport on our network would be encrypted.
- Journaling rules, would allow us to put rules in place to journal emails from specific people (Legal Holds?). The email is sent to a specified mailbox, possibly on a totally separate system. The journaled email contains the original email plus who the email was sent to and by whom. This piece also shows you what distribution list the recipient was on. It also shows CC’ed and Bcc’d recipients.
This ‘stuff’ requires the Exchange Enterprise premium CAL for the Journaling rules. If we go down this path then ALL users would require this CAL. In the past we’ve split users in to those on our network, Enterprise CAL, and those on site (military bases etc.) who only access remotely therefore they’d only need the Standard CAL. With Journaling they’d need the Enterprise premium CAL as well.
Some photos from the 1st day
Where is every one, at the Keynote speech, unlike me.
IT refreshments, yummy lots of processed sugars.
Where’s the sun? Florida is supposed to be sunny and hot. Well I guess one out of two isn’t bad, it is hot.