My remote access from the hotel sucks!, Actually Internet access performance is bad. The performance is so bad that it’s going to take 25 minutes just to update my mailbox. It was pretty bad yesterday so I dropped one of our WAN engineers a note along with a trace route I’d taken. Tonight I did some additional checking and it looks like it’s the local Internet connection that’s the problem. One of the hops is dropping something like 20% of the traffic so I’m going to wait to blog Thursdays sessions. I’ll see if a connection from the conference tomorrow performs better.
Posts Tagged ‘TechEd’
Thursday 12th June – Day 3 of Tech-Ed 2008 – Orlando Florida
Posted by Steven Kennedy on June 13, 2008
Posted in General | Tagged: TechEd | Leave a Comment »
Wednesday 11th June – Day 2 of Tech-Ed 2008–Orlando Florida
Posted by Steven Kennedy on June 11, 2008
Early morning start, got the buss from the Hotel at about 7:30am and got to the Convention center just after 7:45am. Had a quick bit of breakfast and then off to the first session at 8:30am. The first session was on DNS by Mark Misani so I got there a bit early. Just as well as this was one of the larger rooms, 300+ but 5 minutes in to the session the ushers had stopped people coming in until they could find an empty see for them. I’m only going to give a bit of a write up about the DNS session as I’m tired and anyway a couple of the sessions I don’t have slide decks for as they haven’t been posted yet.
I attended six sessions today, one of which was during lunch;
- SVR370: DNS 2008 Style: How Name Resolution Changes in Windows Server 2008 Infrastructures
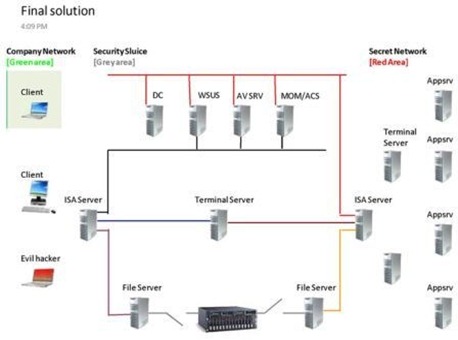
- SEC354: A Hackers Diary: How I Can Hack Your Vulnerable Services and How You Can Stop Me
- LUN61: Do These Ten Things Now or Else Get 0wn3d! – this was the lunch time session
- MBL452: Windows Mobile as Secure as Blackberry: Are You Joking?
- IDA350: Active Directory Rights Management Services (AD RMS)
- SVR384: Licensing Your Windows Vista and Windows Server 2008 Systems: Everything You Know Is Wrong
SVR370: DNS 2008 Style: How Name Resolution Changes in Windows Server 2008 Infrastructures
I’m posting this presentation here. The file is a PowerPoint 2007 file, that’s what Microsoft are using these days. I haven’t tried to convert it to a 2002/2003 format as yet. Mark Minasi has been around a long time, from the DOS days (NOT Denial of Service, Disk Operating System), Marks says he’s 60. He has a deep knowledge of Microsoft Active Directory and networking, including DNS. I have some notes that I need to go through to add to this post but there was one thing that jumped out as being of potential use in cleaning up old DNS domains, that is the ‘DNAME’. This is a new, standards based, DNS record type. You can read about it on slide 37. Simple put what it does is allow you to replace one domain name with another when doing look ups. So that, an acquired company that uses, oh lets say acme.com could use this DNAME record to basically replace acme.com with newcompanyname.com. Now there’s a bit more to it than that, naturally but this would seem to have potential for merging new companies in to our corporate infrastructure.
SVR384: Licensing Your Windows Vista and Windows Server 2008 Systems: Everything You Know Is Wrong
Okay, so I only read the title, not the write up. I thought it was going to be about how Vista, and the bit I was really interested in, Windows Server 2008 is licensed. Boing! wrong. This was about Enterprise Activation of Vista and Windows Server 2008. Licensing, especially last thing in the afternoon, is going to be hard but this …. I did learn a thing or two, between naps (just joking, maybe), that I’ll add to this post once I have re-read my notes. It’s coming up to midnight here and I have a long day ahead of me tomorrow. I get to go to Universal Studios 8:00pm to midnight 🙂
Posted in General | Tagged: DNS, TechEd, Vista, Windows Server 2008 | Leave a Comment »